Let’s assume we have a workstation behind a firewall(NAT) and this workstation isn’t directly reachable from internet. If we want to connect to this workstation from outside, we have to do some tricky things. SSH has an option to create reverse-tunnels. We can connect from this workstation to any ssh-server in internet and we can use that connection to to get back to the workstation.
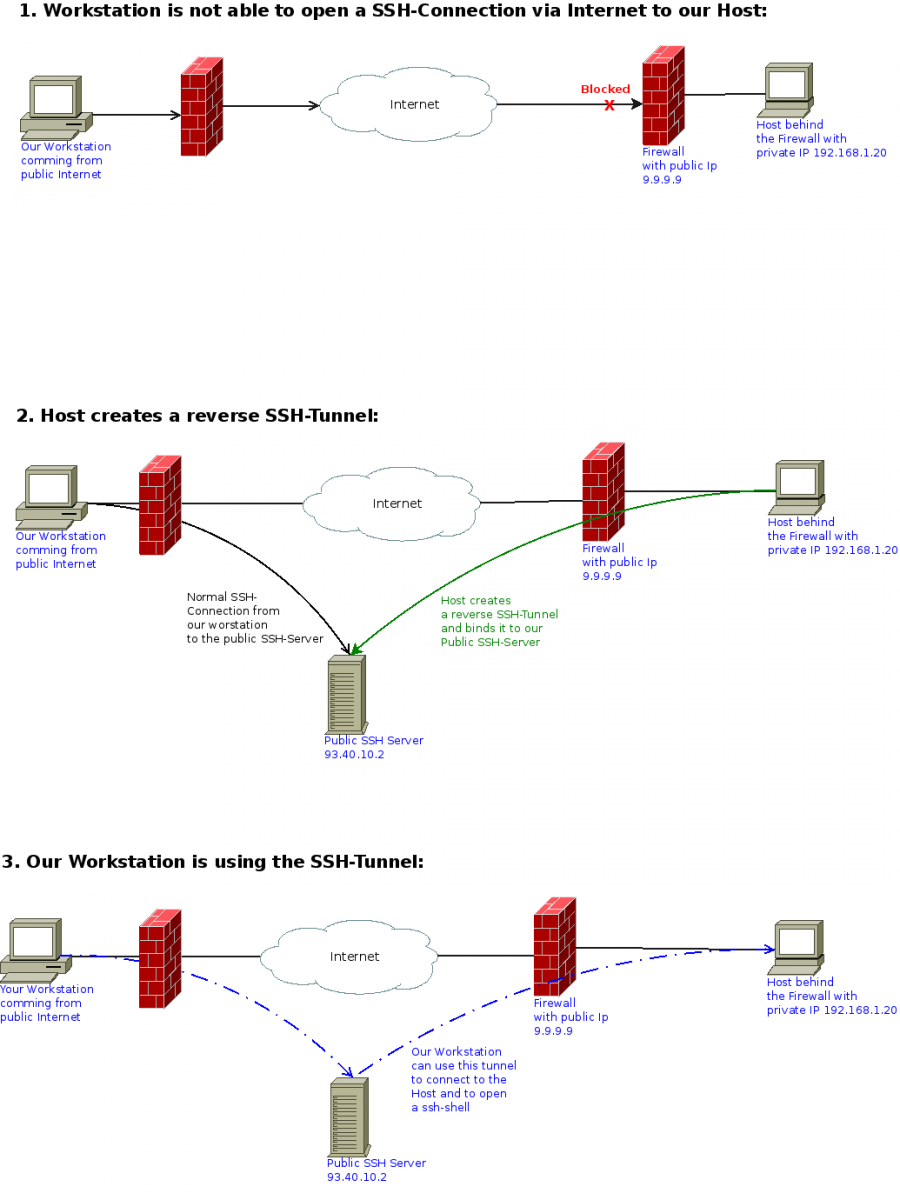
Just to make it clear: we have a workstation out in the internet which is behind a Firewall(NAT). We also have a host which is behind a Firewall(NAT). And we have a public SSH-Server which is reachable from both. You can see that constellation at the picture above.
First we create the Reverse-Tunnel from Host and bind it to Port 2222 at our public SSH-Server:
ssh -R 2222:localhost:22 cooluser@93.40.10.2
It’s important to keep this ssh-session open! I would also recommend to keep the session alive using the command “watch -n 5 date”
Now our workstations also connects to our public SSH-Server:
ssh cooluser@93.40.10.2
If we are connected from our workstation to our public SSH-Server, we can now use the Reverse-Tunnel to connect to the host:
ssh hostuser@localhost -p 2222
You might have recognized that the user has changed. Now we are using any user which exists at our target host.
