| Identifier: | AIT-SA-20240514-03 |
| Target: | FIWARE Keyrock |
| Vendor: | FIWARE |
| Version: | all versions including 8.4 |
| CVE: | CVE-2024-42165 |
| Accessibility: | Remote |
| Severity: | Medium (6.3) |
| Author: | Wolfgang Hotwagner (AIT Austrian Institute of Technology) |
Summary
Insufficiently random values for generating activation token in all versions of FIWARE Keyrock including 8.4 allow attackers to activate accounts of any user by predicting the token for the activation link.
Proof of Concept
The algorithm that is used to create the activation token for user, is predictable. An attacker could predict multiple future “random” numbers and activate any new user:
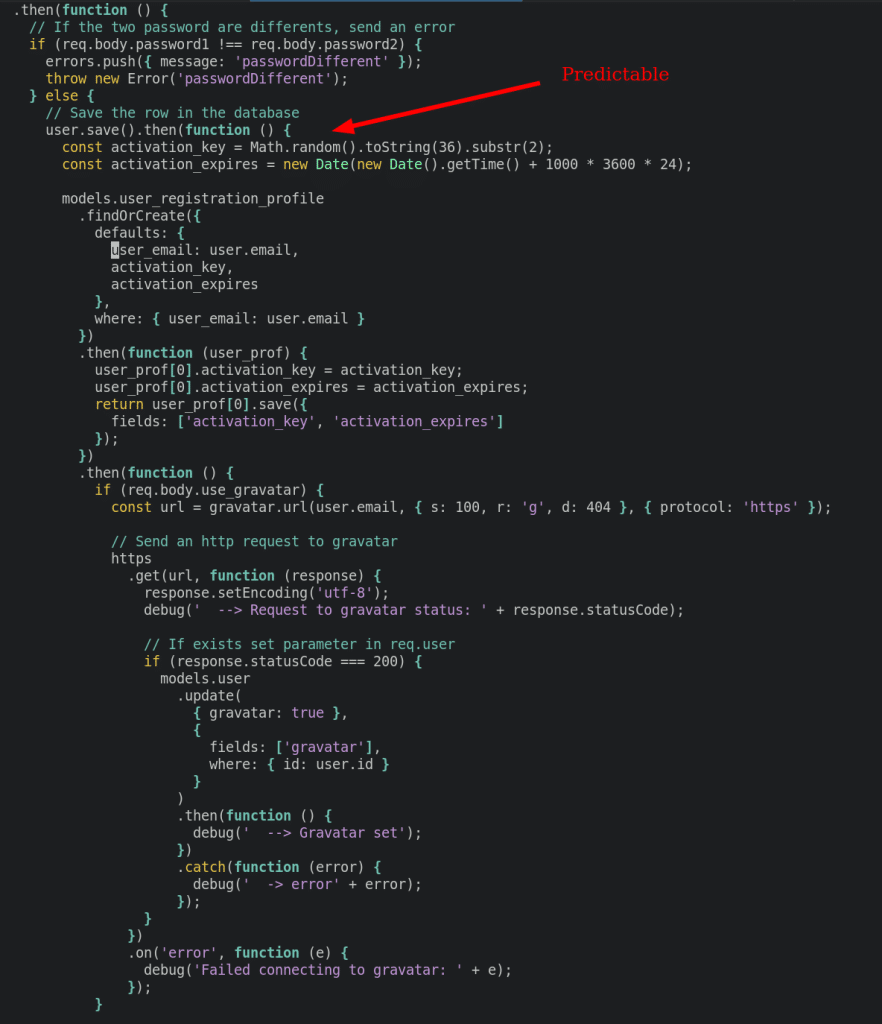
The route to /activate is unauthenticated:
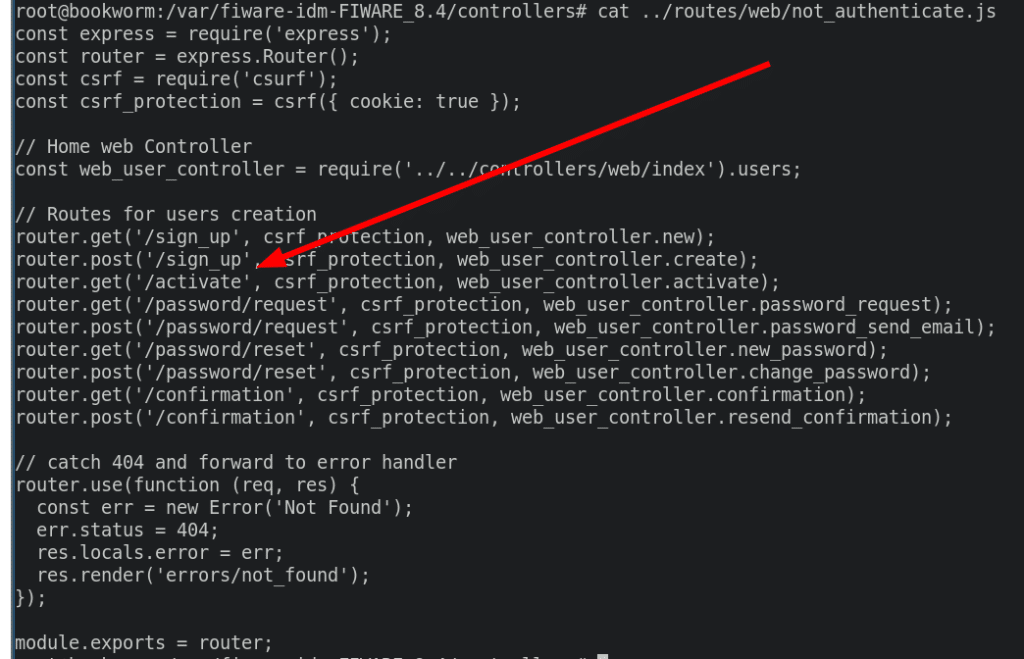
An authenticated non-admin user can create multiple password-reset-token and predict multiple future random keys and use them to activate new users.
For further information see Manipulate passwords of any user
Vulnerable Versions
All versions including 8.4 are affected.
Tested Versions
FIWARE Keyrock 8.4
Impact
An authenticated user can use the password reset token to predict the random number. Using the predicted number the attacker might be able to activate any new user.
Mitigation
Currently (August 12th, 2024) there is no known mitigation.
Vendor Contact Timeline
| 2023-12-19 | Initial contact with FIWARE |
| 2024-03-01 | Asked again about the status |
| 2024-08-12 | Public disclosure |
Advisory URL
[https://pentest.ait.ac.at/security-advisory/fiware-keyrock-activation-of-any-new-user/](https://pentest.ait.ac.at/security-advisory/fiware-keyrock-activation-of-any-new-user/]
