| Identifier: | AIT-SA-20241114-01 |
| Target: | Decidim – The participatory democracy framework |
| Vendor: | Decidim |
| Version: | v0.28 including v0.28.2 |
| CVE: | CVE-2024-45594 |
| Accessibility: | Remote |
| Severity: | High |
| Author: | Wolfgang Hotwagner (AIT Austrian Institute of Technology) |
About
Decidim is a participatory democracy framework, written in Ruby on Rails, originally developed for the Barcelona City government online and offline participation website.
Vulnerability Description
An improper neutralization of input vulnerability in the MeetingIframeEmbedder in Decidim version 0.28.2 allows an authenticated attacker with permissions to propose online meetings, to steal or reuse session data via stored XSS.
Proof of Concept
The embedded URL for new online meetings is not sanitized against XSS injection. A user with permissions to propose online meetings could inject XSS code in a stored meeting to steal information or reuse session-tokens.
Request:
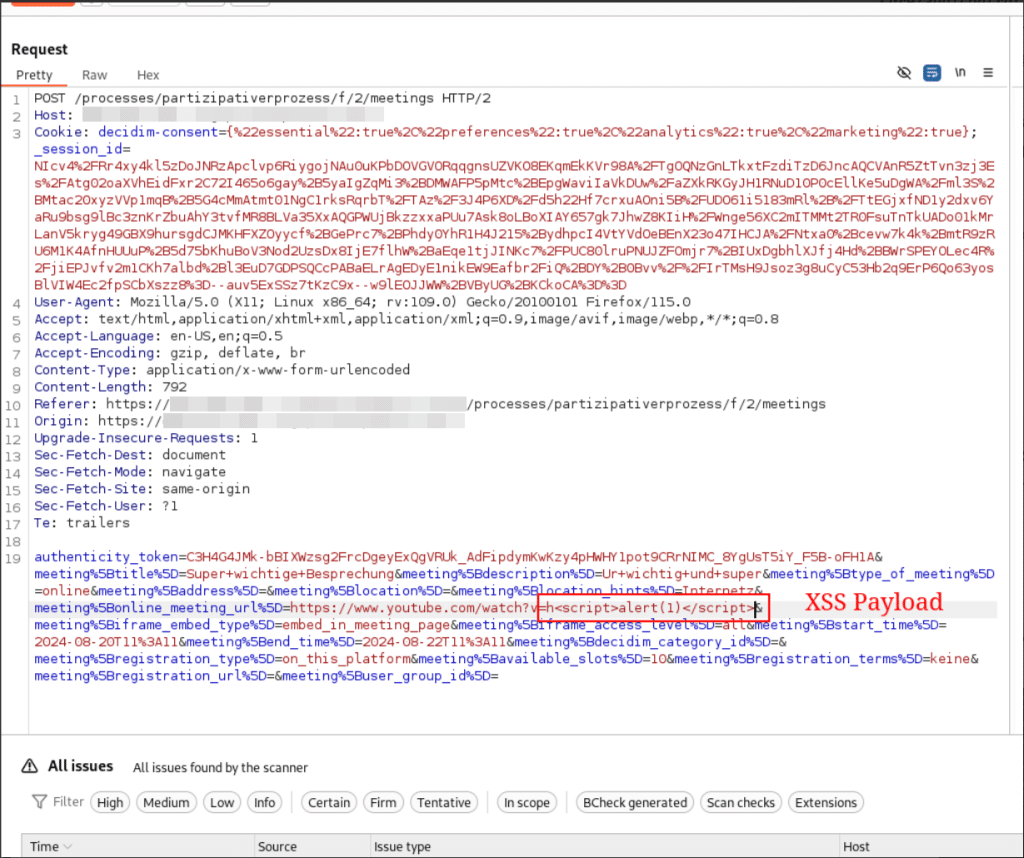
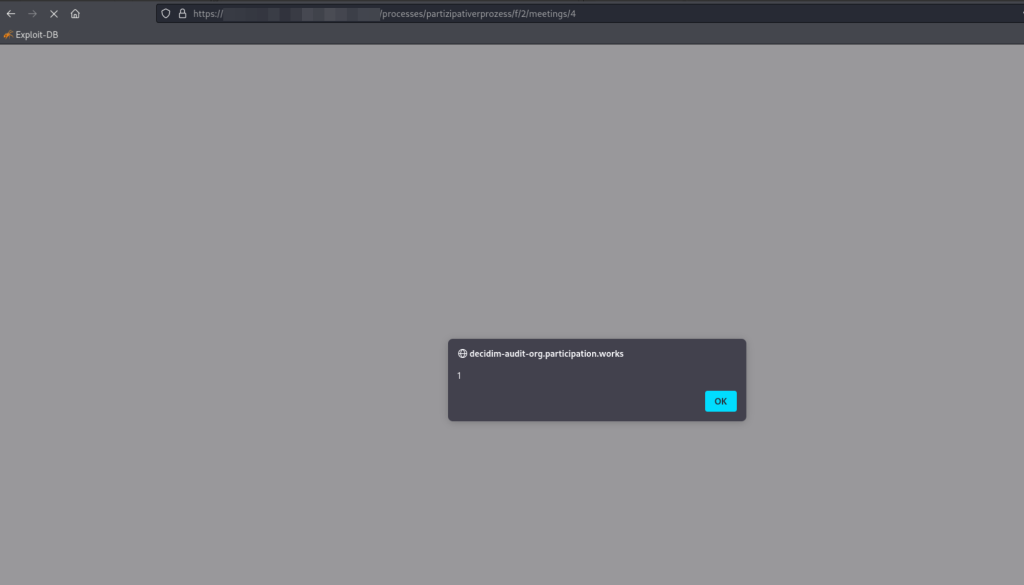
The response indicates that the payload worked properly:
Vulnerable Versions
Version v0.28 including v0.28.2.
Impact
- JS Code Execution
- Escalation of Privileges
- Information Disclosure
Mitigation
Update to Version v0.28.3 or v0.29.0.
Vendor Contact Timeline
| 2024-8-20 | Initial contact with Vendor |
| 2024-8-26 | Vendor confirmed the vulnerability and lowered the CVSS-Score. |
| 2024-11-13 | Public disclosure |
We would like to note that the CVSS score was lowered from 8.7 to 7.7 since the attack complexity was increased to High.
