| Identifier: | AIT-SA-20241112-01 |
| Target: | decidim-module-decidim_awesome |
| Vendor: | Decidim International Community Environment |
| Version: | All versions including v0.11.1 |
| CVE: | CVE-2024-43415 |
| Accessibility: | Remote |
| Severity: | Critical |
| Author: | Wolfgang Hotwagner (AIT Austrian Institute of Technology) |
Summary
Decidim is a participatory democracy framework, written in Ruby on Rails, originally developed for the Barcelona City government online and offline participation website.
Proof of Concept
Content of app/models/decidim/decidim_awesome/paper_trail_version.rb:
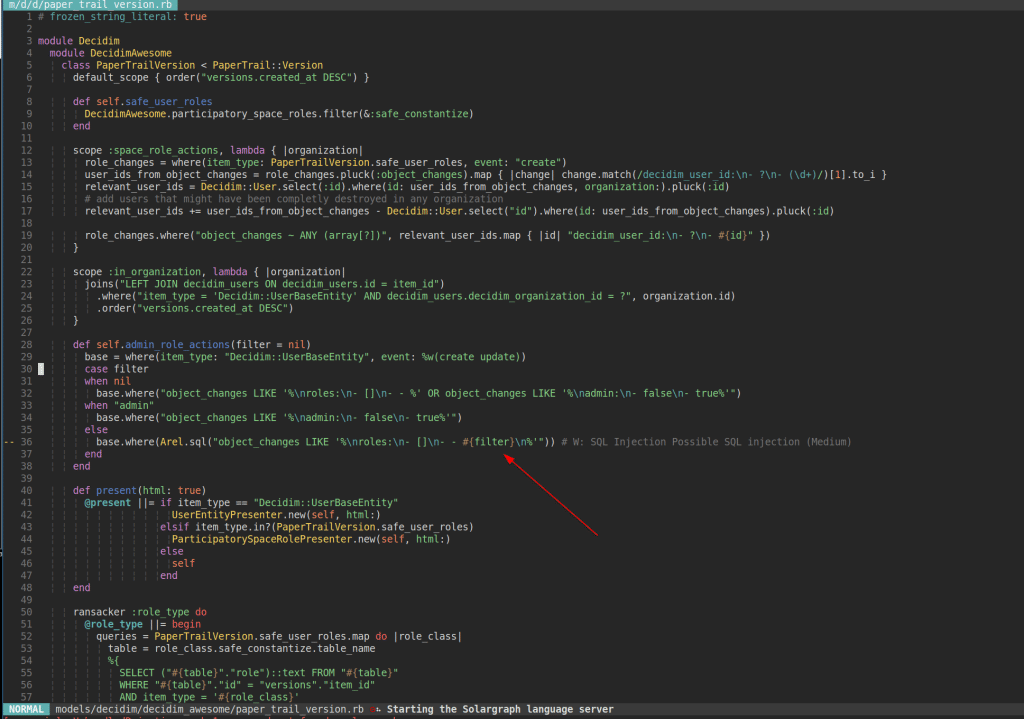
The admin_role_actions method can be executed via AdminAccountabilityController in app/controllers/decidim/decidim_awesome/admin/admin_accountability_controller.rb:
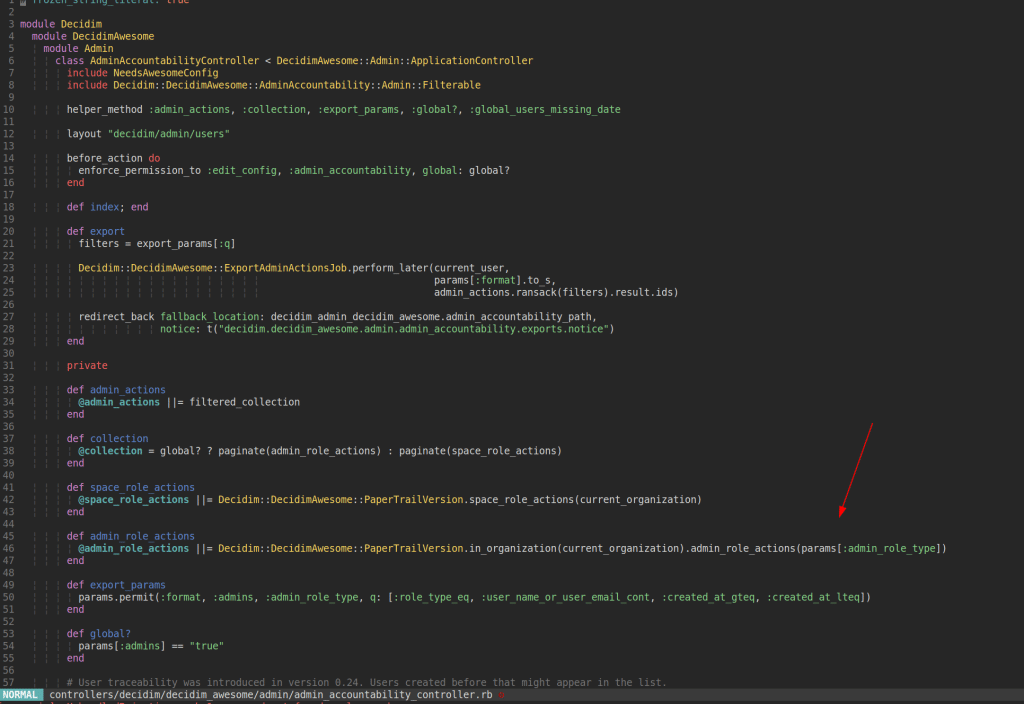
In order to reach that code it is necessary to also include the parameter admins=true. The request to trigger the SQL-injection is:
/admin/decidim_awesome/admin_accountability?admin_role_type=%27);&locale=en&admins=true
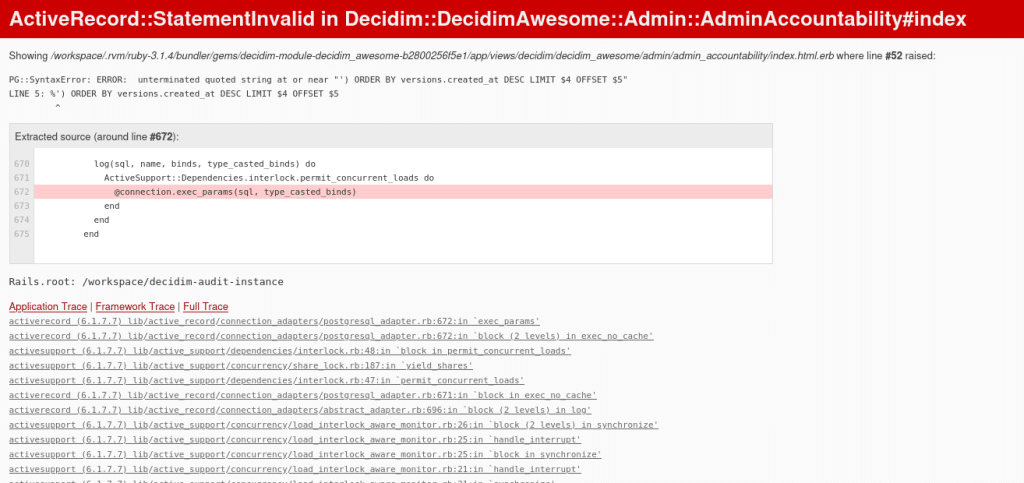
By executing that request the following error indicates that the SQL-injection was triggered:
Vulnerable Versions
All versions including v0.11.1
Impact
- Code Execution
- Escalation of Privileges
- Information Disclosure
Mitigation
- Update to version 0.10.3 or higher.
- Update to version 0.11.2 or higher.
Vendor Contact Timeline
| 2024-8-20 | Initial contact with Vendor |
| 2024-8-21 | Vendor approved finding |
| 2024-8-22 | Update with security fix released |
| 2024-11-12 | Public disclosure |
